What is Discretionary Access Control (DAC)?
Discretionary Access Control, or DAC, is a type of access control system in the field of information security. It gives resource owners the power to decide who can gain access to their resources. This could include files, folders, or entire systems. With DAC, the owners set the permissions. They control who gets in and what actions they can perform.
DAC is known for its flexibility. Resource owners have the freedom to allow or deny access at their discretion. This level of control can be vital for collaboration and security in various environments. Notably, DAC can be personalized. Owners can set access rules that meet their unique needs.
In DAC systems, users are identified through authentication, such as passwords. If the credentials match, access is allowed. What’s crucial about DAC is not just who is given access, but also what kind of access. Owners can assign different levels of permissions based on roles and needs. For example, some users may only view files, while others might edit them.
This system has its roots in the Orange Book of the Trusted Computer System Evaluation Criteria (TCSEC). It’s widely implemented in operating systems and networks. DAC’s principle of owner-controlled access helps to ensure that data remains secure and managed according to the owner’s preferences.

Differences Between DAC, MAC, and RBAC
Understanding how DAC compares to other access control models is key for resource owners. DAC, MAC, and RBAC are the three most common forms of access control. They each have distinct features and use cases.
Discretionary Access Control (DAC)
DAC empowers resource owners to manage access rights. Owners decide who gets to access their resources. It is flexible and user-centric. DAC is ideal for environments where owners need direct control over their resources.
Mandatory Access Control (MAC)
MAC is more rigid than DAC. A central authority, not resource owners, set access permissions. It suits environments needing high levels of security without user control, like military settings.
Role-Based Access Control (RBAC)
RBAC assigns access based on roles within an organization. It is less about individual discretion and more about job functions. RBAC is great for large organizations with many users and complex access needs.
Each model serves different security requirements and organizational structures. DAC is flexible but may lead to inconsistencies in permissions. MAC ensures high security but limits user freedom. RBAC balances the two, offering structured access management.
Core Principles of DAC Access Control
Discretionary Access Control (DAC) stands on several key principles essential for its functioning. These core principles define a DAC environment and guide how access is managed.
Ownership and Authority
In DAC, ownership is the cornerstone. The resource owner has absolute authority to set access permissions. This means they decide who gets in and what they can do. It’s the owner’s call to permit or deny access to others.
Discretion and Control
Flexibility is a fundamental aspect of DAC. Owners have the discretion to change permissions as needed. This control ensures that access measures can adapt to changing needs or situations.
User Responsibility
With power comes responsibility. Users granted access must use resources wisely. Owners trust users with access, expecting responsible and appropriate use.
Authentication and Authorization
Access in DAC systems relies on proper authentication. Users must verify identity through credentials like passwords. Once authenticated, authorization determines the level of access allowed.
Dynamic Access Management
DAC allows for dynamic and ongoing management. Owners can modify permissions on the fly. This agility supports collaboration and prompt response to any security concerns.
Remember, while DAC provides considerable freedom, it must be managed smartly to prevent vulnerabilities. Owners should set clear policies and ensure only trustworthy users gain important privileges.
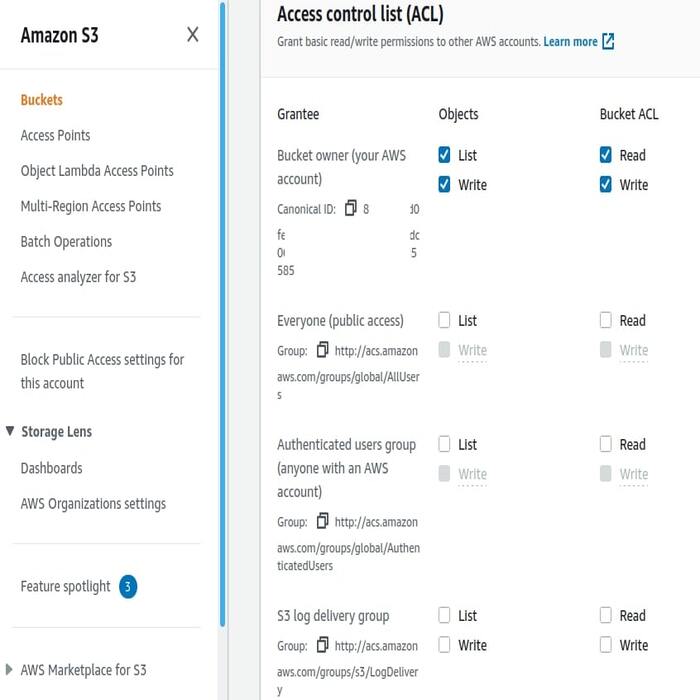
Implementing DAC: Setting Access Levels and Permissions
Implementing Discretionary Access Control (DAC) starts with defining who can access what, and the specifics of their access rights. It’s a critical step to protect resources while enabling sufficient accessibility for users based on their roles and requirements. Here is how you can go about setting access levels and permissions in a DAC system:
- Identify Resource Owners: Determine who owns each resource. Owners have the power to set access permissions.
- Authenticate Users: Ensure users are who they claim to be. Authentication usually involves a username and password.
- Set Access Levels: Assign permissions based on user roles. Permissions can range from read-only to full edit and control rights.
- Create Access Control Lists (ACLs): These lists detail which users have what privileges for each resource.
- Monitor User Actions: Keep logs of user activities to track access and changes made to resources.
- Regularly Review Permissions: Periodic checks help ensure access rights are still appropriate and secure.
By judiciously setting access levels and permissions, owners can harness DAC’s flexibility to enhance both collaboration and security. It’s about striking the right balance between protecting sensitive data and allowing essential data flow within the system. The articulation of DAC policies is vital to mitigate risks and capitalize on the system’s advantages.
Advantages of DAC in Various Sectors
Discretionary Access Control (DAC) systems bring a host of benefits across different sectors. Here’s an overview of the advantages that make DAC an attractive option for various industries.
Flexibility and Control
DAC systems offer unmatched flexibility. Owners can set permissions tailored to user needs. This makes DAC ideal for dynamic environments requiring frequent access updates. Industries like technology and media, where collaboration is key, find DAC particularly beneficial.
Customization for Collaboration
In sectors like real estate, DAC allows custom access for tenants, staff, and visitors. This boosts security while supporting efficient operations. DAC’s customization aids collaboration, as users can share resources according to project demands.
Easy Management in Small-scale Settings
For small businesses and personal use, DAC is straightforward to manage. It avoids the complexity of more stringent systems like MAC. Owners have the ease of controlling access without a heavy administrative burden.
Responsiveness to Changes
DAC’s responsive nature suits sectors facing rapid change. It allows for quick alterations in permissions, vital for sectors like finance and healthcare. Here, user roles can shift, requiring immediate access adjustments.
Improved User Autonomy
DAC empowers users with autonomy over their resources. This leads to better resource utilization and innovation. Creative industries benefit from users having the freedom to manage their work and control access.
Each sector finds unique value in DAC systems, making DAC a versatile and widely implemented access control approach. Its adaptability and user-centric model are key to its prevalence across diverse industries.
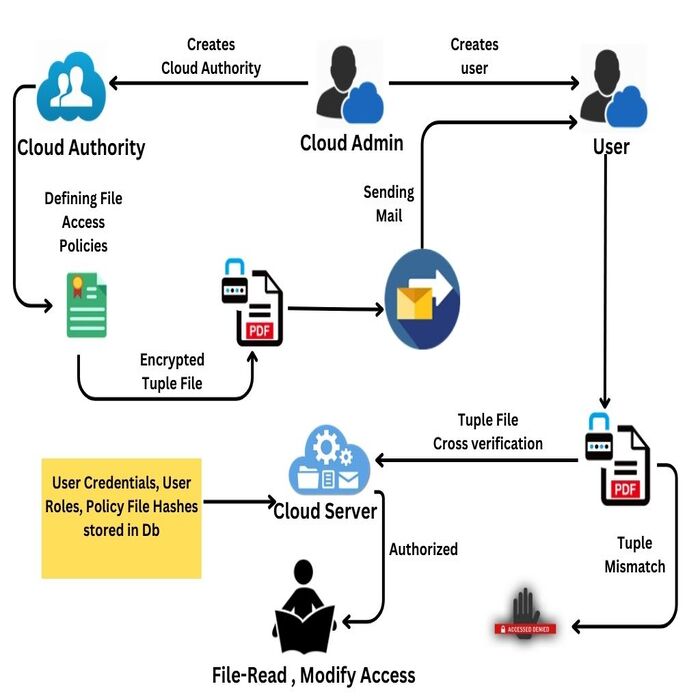
Potential Vulnerabilities and Risks of DAC Systems
While Discretionary Access Control (DAC) systems empower owners with high flexibility, they’re not without their fair share of vulnerabilities and risks. It’s crucial to know these to better protect resources and data.
Broad Access Permissions
One risk is granting too broad access permissions. This can lead to data breaches if not managed carefully. Owners should grant access that’s necessary, not more.
Inconsistent Policies
Another issue is the potential for inconsistent policies. If owners set rules on a whim, the system may end with conflicting permissions.
Insider Threats
DAC systems could also face insider threats. Disgruntled employees with access could misuse their privileges, leading to data compromise.
Exploitation of Weaknesses
Weak authentication methods, like simple passwords, can be easily hacked. Stronger verification measures are essential to prevent unauthorized access.
Lack of Centralized Control
DAC’s decentralized nature can make it hard to monitor and control access uniformly. This can allow vulnerabilities to go undetected longer.
Inadequate Logging and Monitoring
Without proper logging and monitoring, detecting unauthorized changes becomes difficult. Organizations must invest in robust monitoring tools.
Owners and administrators must be aware of these potential risks and take steps to mitigate them. Regularly updating access privileges, employing strong authentication methods, and comprehensive monitoring are indispensable. Recognizing the potential downsides helps in crafting a DAC system that is secure, reliable, and efficient for all users.
Best Practices for Managing and Securing DAC Environments
Effective management and strong security are key to leveraging the full potential of DAC access control systems. Here are best practices for ensuring these systems are both efficient and secure:
Set Strong Authentication Protocols
Use complex passwords and multi-factor authentication to ensure only authorized users gain access.
Regularly Update Access Permissions
Review permissions frequently. Adjust as roles or business needs change to keep access current and secure.
Limit Access on a Need-to-Know Basis
Give users the least privilege needed for their tasks. This reduces the risk of data breaches.
Employ Robust Monitoring and Logging
Track user activities and access changes. This helps spot unauthorized actions and reinforces accountability.
Establish Clear DAC Policies and Procedures
Create firm rules for setting and altering access. Educate users on these policies to avoid confusion.
Back Up Data Consistently
Ensure data is regularly backed up. This protects against data loss in case of errors or breaches.
Conduct Regular Security Audits
Assess your DAC system’s security measures. Fix any vulnerabilities to prevent exploitation.
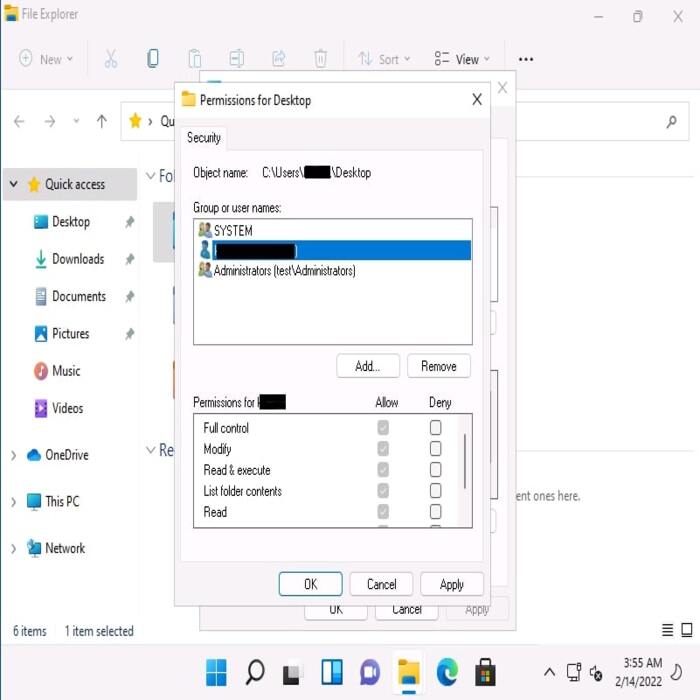
Use Access Control Lists (ACLs) Wisely
Configure ACLs carefully. Make sure they accurately reflect current access needs and privileges.
By following these best practices, DAC environments can be managed efficiently, keeping resources secure while optimizing usability.
Future of DAC Access Control in Cybersecurity
The future of Discretionary Access Control (DAC) in cybersecurity looks to balance flexibility with security. As cyber threats evolve, so must DAC. The system will likely become smarter, integrating advanced authentication methods like biometrics or AI-driven behavior analysis. This integration aims to strengthen security without sacrificing the user-friendly nature of DAC.
In the coming years, we may see DAC systems that learn from user behavior. These systems could auto-adjust permissions based on threat analysis and user patterns. Another development could be the broader use of encryption within DAC systems. This would protect data even if breaches occur.
Moreover, DAC could increasingly mesh with other access control models to form hybrid systems. These hybrids can offer the best features of each model. For instance, DAC for user convenience alongside MAC for tougher security measures. Cloud technology is expected to play a big role too. It allows for seamless, scalable DAC implementations across distributed networks.
Collaborative tools and remote work are on the rise, pushing DAC towards more robust online systems. They must secure sensitive data while allowing for ease of sharing and collaboration. Expect to see more emphasis on user training as well. Educated users are key to a secure DAC environment since they help prevent insider threats and recognize phishing attempts.
The goal is clear: a DAC access control that is robust, intelligent, and agile. It must protect against today’s threats while being ready for tomorrow’s challenges. Continuous innovation and vigilance are the path forward for DAC in cybersecurity.