Introduction to Broken Access Control Risks
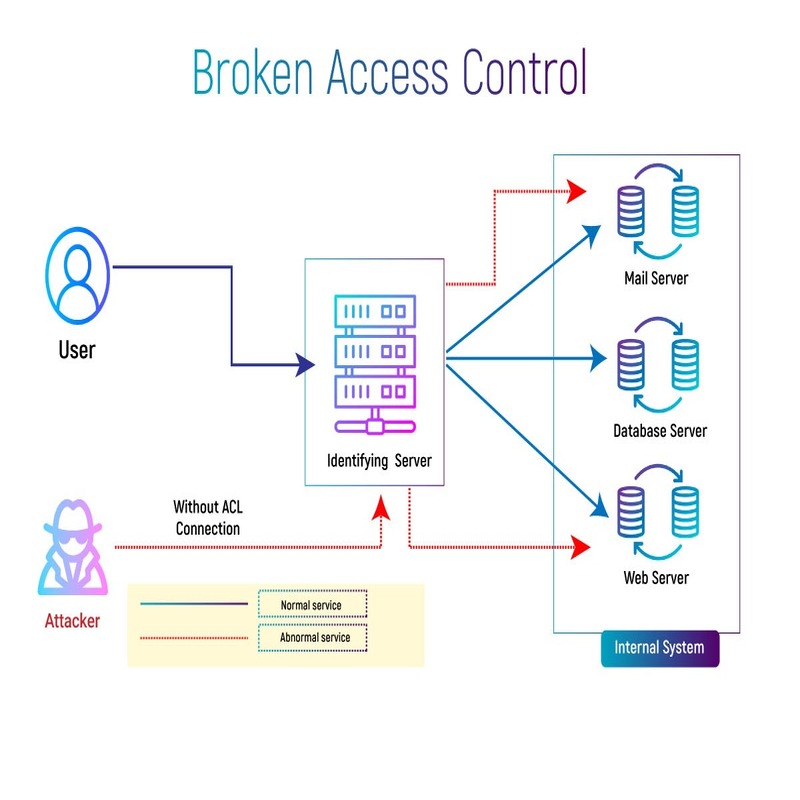
When it comes to web security, one of the main hazards is broken access control. This problem happens when people get to see, change, or erase data they shouldn’t be able to. Imagine if someone without the right access could peek at private customer details, meddle with financial records, or grab admin rights. The stakes are big: money loss, damaged reputation, strict legal penalties, and even a blow to your competitive edge in the market.
Understanding what broken access control is and its gravity is key. It’s essentially when your app doesn’t check properly who gets to do what. If controls are weak, they might let users do things beyond their roles. The result? Serious risks for businesses and their clients. It’s like leaving your car unlocked with the keys in it – not a smart move. So, getting a firm handle on authorization checks and steering clear of these vulnerabilities is critical to protect your digital assets and the trust of your customers.
Top Ranked Security Threat: OWASP Perspective
The Open Web Application Security Project, or OWASP, plays a big role in web security. They put broken access control on their list of top dangers nearly every year. This list, known as the OWASP Top 10, alerts us to what we need to watch out for the most. Given OWASP’s focus, it’s clear that fixing broken access control is a must.
Why does OWASP care so much about this? Because when access control breaks, it opens doors for bad actors. They can sneak into areas they have no right to be in. The damage can hit your wallet, ruin your company’s name, land you in legal trouble, and give your rivals a leg up. For OWASP, the message is loud and clear: pay attention to broken access control if you want to keep your app and data safe.
OWASP offers advice and tools for this. They help software folks build safer systems. Their top 10 list helps us understand what specific attack types threaten our applications. That way, we can create better defenses against them.

Common Techniques Used in Broken Access Control Attacks
Broken access control attacks can happen in many different ways. To stop them, we must first understand these methods. Below are common techniques attackers use to break access control.
Parameter Tampering
Attackers change URL parameters or form fields to gain unauthorized access. For example, they can change a user ID in a URL to see someone else’s shopping cart.
Horizontal Privilege Escalation
Here, attackers gain access to another user’s level of privileges. They might steal a session ID to get into another person’s account.
Vertical Privilege Escalation
This technique allows attackers to access higher-level privileges. For instance, an attacker might find a loophole to use admin-only features without proper rights.
Data Exposure Through Public URLs
Sometimes, sensitive data gets exposed because of errors or misconfigurations. URLs that should be private might become accessible to anyone.
API Abuse
Attackers target web APIs. They manipulate API endpoints or inject harmful data to unlock information and actions they should not reach.
Understanding these common attack patterns is crucial for creating effective defenses against broken access control. Remember, attackers are always finding new ways in, so our security must be up-to-date and tough.
Understanding Broken Access Control Vulnerability Types
Broken access control (BAC) refers to security issues where users can access what they shouldn’t. This can include viewing private info, changing another person’s account data, or using admin powers without permission.
Insecure Direct Object References (IDOR): Attackers change the URL to reach hidden data. For example, they might see someone else’s order on a shopping site by tweaking the order number in the link.
Excessive Permissions: Sometimes users have more access than they need. This can let them do things they shouldn’t, making systems vulnerable.
Bypassing Access Controls: Attackers can slip past security using flaws like SQL injection. This way, they might get admin access or see private data.
Weak Session Management: Poor session controls can lead attackers to take over someone’s account and pretend to be them.
Privilege Elevation: Here, someone with limited access might find a way to get higher-level powers.
Understanding these types helps us defend better. It’s crucial to keep an eye on how users can wiggle past rules and plug those gaps.
Five Proactive Measures to Combat Broken Access Control
Dealing with broken access control means taking action before things go wrong. Here’s how to be proactive.
1. Validate Inputs Rigorously
Check every user input carefully. Make sure the data coming into your app is clean. This blocks bad data that can lead to security gaps.
2. Stick to Least Privilege
Give users only the access they need. Nothing more. This limits risks if an attacker breaks in.
3. Block Code Injection
Keep your app safe from code injection. Use techniques that check input, like whitelisting. Stay clear of attacks that can sneak past access checks.
4. Strengthen Session Management
Manage sessions well. Use secure tokens and set time-outs. This can help prevent attackers from hijacking user sessions.
5. Monitor and Test Security
Always test your app for weak spots. Do this often. Keep an eye on logs to spot anything fishy. Fix problems fast to keep your defenses up.
These five steps can help keep your guard up and kick broken access control to the curb. Regular updates and patches are key, too. They shut down new ways attackers find to try and break in. Use these measures, and you’ll make it tough for the bad guys to get through.
Addressing the Common Misconception: Client-side vs Server-side Security
It’s crucial to clear up a big mix-up in web security. That’s about client-side vs server-side security. You can’t rely on just one to stop attacks. Here’s a simple rundown on each and why both matter a lot.
Why Client-side Security Alone Won’t Cut It
Let’s talk about client-side security first. It checks things on the user’s web browser. This includes making sure form info is correct. But here’s the thing – it’s not enough on its own. Keen hackers can bypass these checks easily. They can tweak the web browser or interrupt the server requests. So, if you just have client-side checks, you’re not really safe.
The Strength of Server-side Security
Now, let’s look at server-side security. This happens on the website’s server after getting user info. It’s tougher for hackers to mess with. Server-side checks happen out of their reach. That’s why they’re more reliable in protecting your app. But remember, even server-side checks need backups. You must still have proper checks on the client side.
Integrating Both for Optimal Protection
The key to solid security? Combine both types. Use client-side checks for a first defense. Then, bring in server-side checks for a full guard. By mixing the two, you block different ways hackers can try to get in. It’s like having a double door lock – much harder to break through.
To really deal with broken access control, make sure to get these basics right. Check your user inputs thoroughly on both ends – in the browser and on the server. By doing so, you handle many risks right from the start. And always stay alert for new threats to keep your security up to date.

Engaging Expertise for Enhanced Application Security
As we’ve explored, broken access control poses real risks to app security. Experts can offer deep insight and advanced tactics to tackle these issues. Let’s see how calling in pros can beef up your defense.
Turn to Specialists for Deep Dives
Hire security experts for an in-depth look at your system. They can spot weak spots and suggest fixes. Specialists know the latest threats and how to stop them. They bring know-how that can make your app much tougher to crack.
Use Advanced Tools and Strategies
Experts use top tools and approaches to shield apps. They can set up smarter access checks and monitor for suspicious behavior. Advanced software helps them stay one step ahead of hackers.
Regular Security Audits and Upgrades
Pros can do regular app check-ups to find and fix problems. Keeping the app updated can shut off ways for attackers to get in. Experts ensure that your security grows with new tech changes.
Tailored Protection Plans
Specialists create security plans that fit your app’s needs. They don’t just use one-size-fits-all solutions. They tailor the security to handle specific risks your app faces.
Training and Awareness
Experts also train your staff on security best practices. They teach teams how to spot risks and react right. Knowing what to look for can be a game changer in stopping breaches.
In short, for the strongest shield against broken access control, pair up with security whizzes. Their expertise can help you build a resilient system. Plus, they can train your team to be alert and react fast when needed. Remember, the aim is to stay steps ahead of any potential threats. With expert help, your app can stand tough against today’s sneaky hackers.


